EMnify Core Network security
The EMnify Core is deployed over Amazon Web Services (AWS). It is utilizing the security mechanisms provided by AWS for controlling access to the platform. It is also securing the data exchanged between the different components of the EMnify core. These mechanisms include VPC, secure links based on VPN and firewalls.
Security of the communication to/from the devices
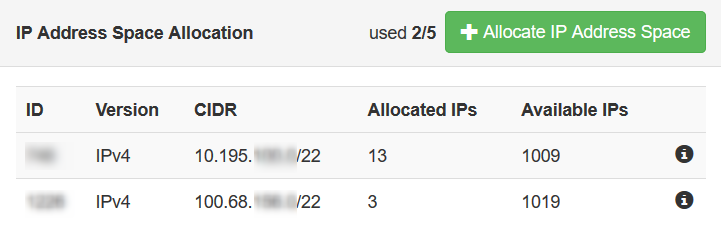
Private IP address space
In the default configuration each EMnify customer is provided with a private IP address space that can host up to 1.022 different IP addresses. This IP address space has the form of a /22 subnet. The customer can add up to 5 different IP address spaces per account.
An endpoint represents a mobile device with an assigned IP address in the EMnify control platform.
All the endpoints created by a customer will be assigned a private IP address. Private means that each IP address is not exposed to the risk and threats of the public Internet.
VPN
VPN (Virtual Private Network) is the solution to allow the communication of sensitive data through an open network, like the Internet, while at the same time maintaining the security and privacy advantages of the private IP space.
VPN encryption
A VPN provides a secure connection between a user and an IoT device. Even when data being transferred between you and a device is “sniffed” by a third party, encrypted VPN data only appears as incomprehensible characters. Data in this form would take a great deal of time and resources to decrypt, making it unlikely for anyone to do so. Also, when you and IoT devices communicate through VPN, your geographical locations are hidden from view.
VPN is optimal for IoT Devices
IoT devices are often developed with very low computing power as a complex system is not necessary to perform most IoT tasks. Many IoT devices consist of a microcontroller, sensors and a GSM module, making it difficult to implement robust device encryption. When an IoT device communicates over the public internet, the unencrypted data it transfers is easily susceptible to attackers. By implementing a VPN between the IoT application server and the EMnify EMcore platform, all traffic is fitted with strong encryption before it is sent over the public internet. Additionally, this process is completely transparent for the mobile device and does not require special hardware or any additional configuration on the IoT device itself.
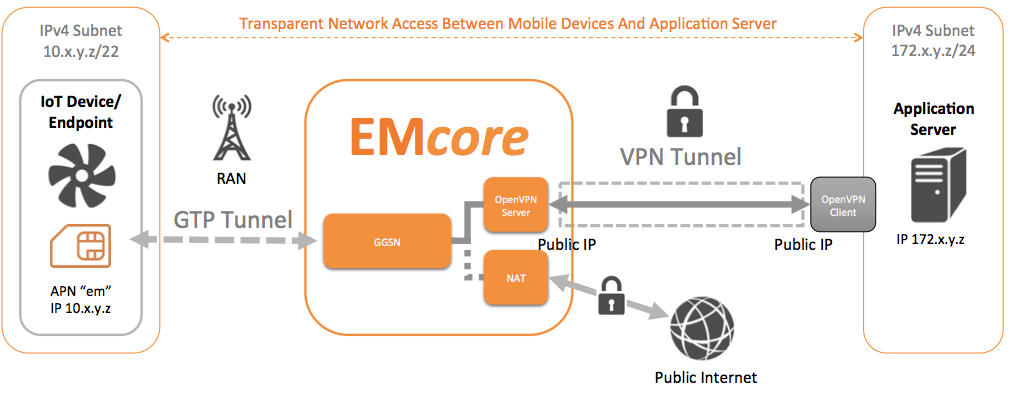
Available VPN options
EMnify offers currently two different VPN solutions: 1) OpenVPN, 2) IPsec Tunnel
Option 1 - OpenVPN
OpenVPN is an open-source software that utilizes the security protocol SSL/TLS. It has strong features and is known for its ease of implementation. It allows customers to authenticate each other using a pre-shared key.
OpenVPN works in a client-server mode, meaning OpenVPN users connect to the OpenVPN server and from there have full access to the internet. It is recommended by EMnify for most use cases from start-up through medium-sized businesses who require a high level of security but are comfortable with the flexibility of an opensource software. Users of OpenVPN can have either dynamic or static IP addresses, and the software is increasingly becoming available on most operating systems.
Option 2 - IPsec Tunnel
Internet Protocol Security (IPSec) sets up a tunnel from a remote device to a central business server. It is designed specifically for internet traffic and ensures private, secure communication over the public internet by cryptographic security services.
IPSec is recommended for large, global enterprises, especially when multiple peers and security layers are used. IPSec requires a static IP address, and technical resources to be implemented.
Larger enterprises are more inclined to have the needs and resources to overcome these barriers. A harder technical set-up also makes this VPN option the only one that EMNify charges to implement and maintain.
The other strong case for IPSec exists when dealing with data of a very sensitive nature such as the transfer of personal identification information.
Kommentare
0 Kommentare
Bitte melden Sie sich an, um einen Kommentar zu hinterlassen.